Did you miss a session on the Knowledge Summit? Watch On-Demand Right here.
GreyNoise Intelligence as we speak unveiled a brand new device that goals to assist safety groups to extra simply block recognized attackers who’re in search of to use crucial vulnerabilities on a big scale.
All through the previous two years, an particularly “large, unhealthy and scary” vulnerability has cropped up about as soon as each two months or so, says GreyNoise founder and CEO Andrew Morris. The invention of such vulnerabilities inevitably results in a scramble amongst cybersecurity professionals, and “everybody freaking out about it,” Morris mentioned.
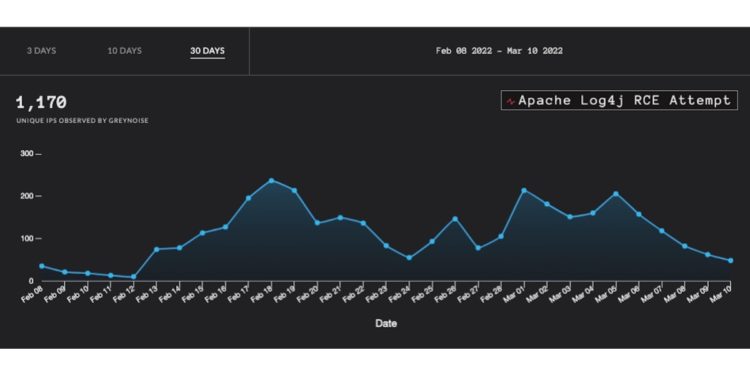
The most recent was the vulnerability referred to as Log4Shell, an simply exploited distant code execution (RCE) flaw in Apache Log4j. The RCE vulnerability within the broadly used logging software program part was disclosed on December 10.
The vulnerability in Log4j “was notably unhealthy,” Morris mentioned. “However it made us understand, it’s simply going to maintain occurring.”
GreyNoise operates sensors in a whole bunch of information facilities worldwide, capturing information from across the web that may pinpoint malicious actors and their exercise. Shortly after the disclosure of the vulnerability in Log4j, the Washington, D.C.-based startup launched its trove of information totally free to the general public.
Now, with its new device, Examine 4.0, GreyNoise is aiming to streamline what it did for Log4j for future vulnerabilities which are particularly extreme. The device will present defenders with entry to info that they will use to make choices — in addition to a solution to extra simply do automated blocking for IP addresses which have been making an attempt to use the vulnerability, Morris mentioned.
Defending in opposition to exploits
For safety groups, utilizing the device will be capable of purchase them a while whereas they patch their methods, he mentioned.
“The technique is, attempt to get out forward of it as greatest we are able to and get as a lot info as attainable about whose exploiting the vulnerability at scale. After which, get that info to as many individuals as attainable — in as low-friction a approach as attainable,” Morris mentioned.
The way in which that GreyNoise has determined to do this is by offering dynamic block lists, which “individuals can feed right into a ton of various safety merchandise — that simply mechanically replace with the IP addresses of all the hosts which are exploiting a vulnerability at scale,” he mentioned. “So individuals can principally punch it in and simply stroll away.”
Examine 4.0 is aimed toward defending in opposition to opportunistic “scan-and-exploit” assaults — involving vulnerabilities that have an effect on the perimeter and are being exploited at a big scale. Along with Log4Shell, different vulnerabilities which have match this standards embrace the Pulse Safe VPN vulnerability, EternalBlue (which was exploited within the WannaCry ransomware assaults), Azure “OMIGOD” and the latest Apache path traversal vulnerability, in response to Morris.
Key capabilities for the GreyNoise Examine 4.0 device embrace fast triaging of alerts based mostly on classifications of the alerts as malicious, benign or focused, and identification of trending internet-based assaults which are concentrating on sure vulnerabilities. The device will even permit customers to dam and hunt for IP addresses which are opportunistically attacking a sure vulnerability, in response to GreyNoise.
‘Much less friction’ for customers
With the brand new device, “we’re actually simply making an attempt to repeat what we did for Log4j — besides do it at scale, do it on a regular basis and do it with lots much less friction for the consumer,” Morris mentioned.
For customers which have a free account with GreyNoise, the consumer simply has to repeat the hyperlink for a specific vulnerability after which feed that hyperlink into their safety device — equivalent to a next-gen firewall or risk intelligence gateway, he mentioned. The device will then regularly pull within the dynamic block record, to maintain the record of unhealthy hosts up-to-date, and can block these unhealthy hosts, Morris mentioned.
GreyNoise, which has about 100 paying prospects, is within the strategy of determining what options to supply to these prospects on prime of the free capabilities, he famous.
In the end, GreyNoise is in search of to study from the Log4j expertise, “in order that the subsequent time this occurs — which it can — we’re somewhat bit extra well-prepared,” Morris mentioned. “We wish to do as a lot as we are able to to make the issues suck much less, for as many individuals as attainable.”